SOC 2 Type II Compliance
We undergo an annual SOC 2 Type II audit that is performed and delivered by CPA firm, KirkpatrickPrice. The audit specifically tests our reporting controls that relate to security, availability, confidentiality, and privacy.
This attestation provides evidence that we have a strong commitment to security and to delivering high-quality services to our clients by demonstrating that we have the necessary internal controls and processes in place.
Successfully completing the SOC 2 Type II audit highlights our continued commitment to deliver effective solutions and safeguards that protect and secure ours and our customers’ data.
In the video below, Joseph Kirkpatrick of Kirkpatrick Price, an information security auditing firm, describes our security mindset when it comes to data, projects, and records.
Our Secure System Helps You Become A Better Data User
We’ve designed our processes and systems to prioritize and maximize data security in all aspects of our digital conversion solutions. We know that we need to be prepared to face today’s threats confidently, which is why we value implementing security into all our processes.
When you work with us, you’ll inherit comprehensive controls designed to secure our data and yours.
Proof of these controls is achieved through compliance with the SOC 2 Trust Services Criteria.
Joseph Kirkpatrick of Kirkpatrick Price, an information security auditing firm,
and Will Whitney of BMI discuss BMI’s culture of security and how it’s evolved.
Joseph Kirkpatrick of Kirkpatrick Price, an information security auditing firm, and Will Whitney of BMI
discuss how project security controls are utilized at BMI and how they benefit clients.
Joseph Kirkpatrick of Kirkpatrick Price, an information security auditing firm,and Will Whitney of BMI
discuss what it’s like for BMI to go through a SOC 2 Type II audit.
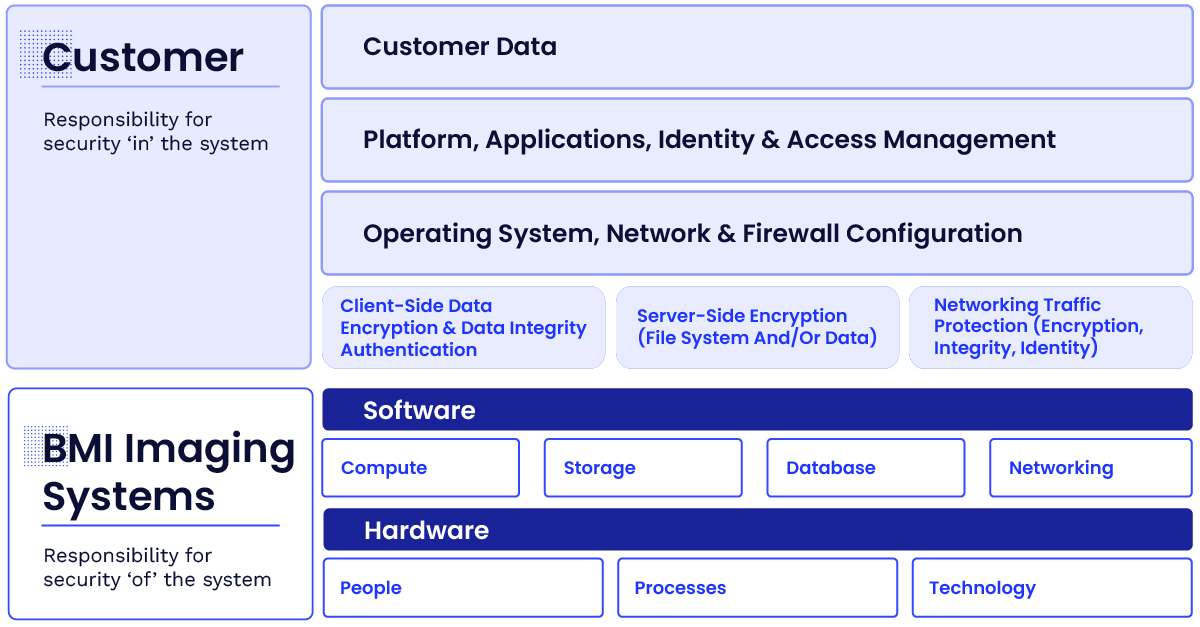
Security & Compliance Are Shared Responsibilities
As one of our clients, you benefit from our policies, architecture, and operational processes built to satisfy the requirements of industry standards and best practices.
Additionally, you’re responsible for the use and management of the system and the data added to it.
When these two elements work together properly, you can be confident in the security measures designed to protect your data.